Enforce MFA on the Azure Portal using Conditional Access
Improved security by increasing re-authentication frequency
When increasing security in Azure, the first place to look at is the portal. Even though initially authenticating, preferably you want to enforce Multi-Factor Authentication (MFA) and re-authentication at regular intervals so if a device is compromised, you are lowering the risk. In this post, I will explain what is Conditional Access and walk through the steps to configure a Conditional Access policy that will frequently enforce MFA.
Be aware:
The Cloud app we are selecting as part of the configuration also applies to other Microsoft services so please refer to the latest documentation for the list of affected services.
What is Conditional Access
Conditional Access is like using If and Then statements where you can configure different access practices based on factors like device type, location, user risk, etc.... This type of practice is a modern and flexible approach, allowing you to configure Cloud apps with different authentication requirements. You can read more about Conditional Access by reading Microsoft documentation on the tool.
We will be utilising Conditional Access to:
- Enforce on particular users
- Apply to Azure Management Endpoints (including Azure Portal)
- Require users to use MFA on access to the specified application(s)
- Sign-in frequency to be every 1 hour (re-authenticate using MFA) when using the application(s)
Conditional Access Configurations
- Within the Azure Portal, search for Azure AD Conditional Access;
- Select the New policy option;
- Give the policy a Name that is identifiable;
- Open the User and groups settings, I would recommend selecting a particular user or group to include in this policy. Make sure you initially exclude yourself and/or other administrators to prevent lockout of the portal;
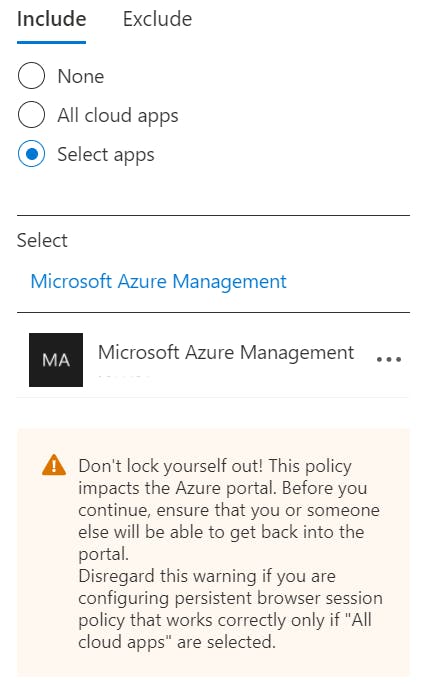
- Select Cloud apps or actions and make sure the Select what this policy applies to is toggled to Cloud apps. Under the heading Include, click the radio button with the name Select apps and from the Select option search for Microsoft Azure Management app and add this;
- Within the Conditions settings, you can configure how this policy applies to a user based on factors like device type, risk, etc... I left the configuration as default but you can configure this based on your requirements;
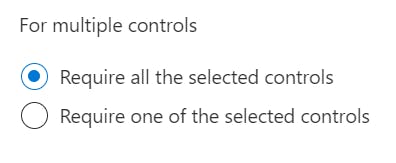
- Expand the Grant settings, select Grant access and Require multi-factor authentication.
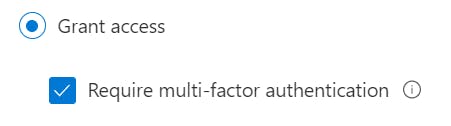 Under the multiple controls heading, select Require all the selected controls;
Under the multiple controls heading, select Require all the selected controls;
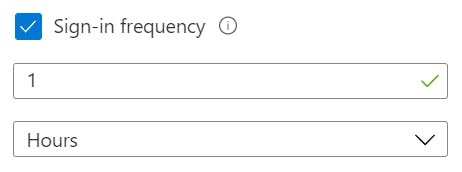
- Open the Session settings, select Sign-in frequency and configure the amount of time before MFA is required again. I have configured 1 hour but configure this to what feels suits your needs;
- Final option is to select Report-only or On for enabling the policy. Report-only is always recommended to then review logs and then enable once confident;
- Once happy with the configurations that are set, click Save.
Allow a small period of time for the policy to kick in but you can then try accessing the Azure Portal using a user who has the policy applied to them. You will automatically be prompted to identify yourself by approving access using MFA.

