Table of contents
Microsoft Sentinel allows integration with your DevOps platforms, including GitHub. It enables us to monitor, alert, and create automated responses based on the generated audit logs.
In this post, we will cover how to connect GitHub to Microsoft Sentinel. It includes any configurations required within GitHub and Sentinel and testing that the connection works once we have completed the integration.
Prerequisites
- Admin access to the GitHub organisation that allows access to the GitHub audit logs
- Admin access to Microsoft Sentinel
- The GitHub organisation requires an enterprise subscription to enable Auditing.
Personal Access Token (PAT)
We will start by generating a PAT to establish a connection to our organisation. I recommend generating a PAT using a system account. What I mean by a system account is a user account that is not assigned to any particular user but used in situations where integration between GitHub and a third-party tool is required. When users leave the org or something happens to their account, it prevents the integration from breaking.
Open Settings by selecting the profile picture at the top right of the GitHub site.
From the side menu, you should see at the bottom of the list Developer settings, select to continue.
Again, from the side menu, select Personal access tokens
Click the Generate new token button.
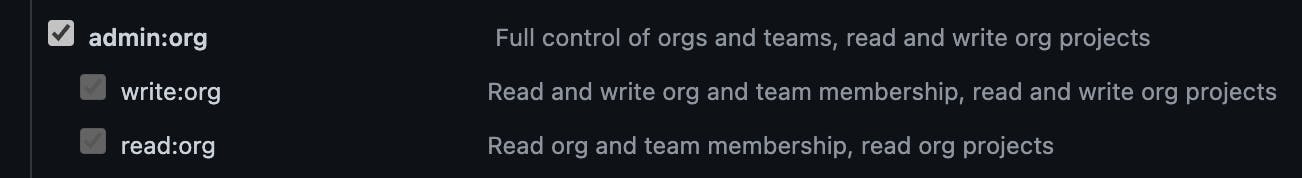
Give the PAT an appropriate reference within the Notes field, and set the expiration following your organisation's security policies. You will need to select at least the admin:org scope so when the PAT can is used, it will have the correct permissions to access the audit logs.
When you are ready, select the Generate token button.
Please keep a record of the token and store it safely.
Data Connector
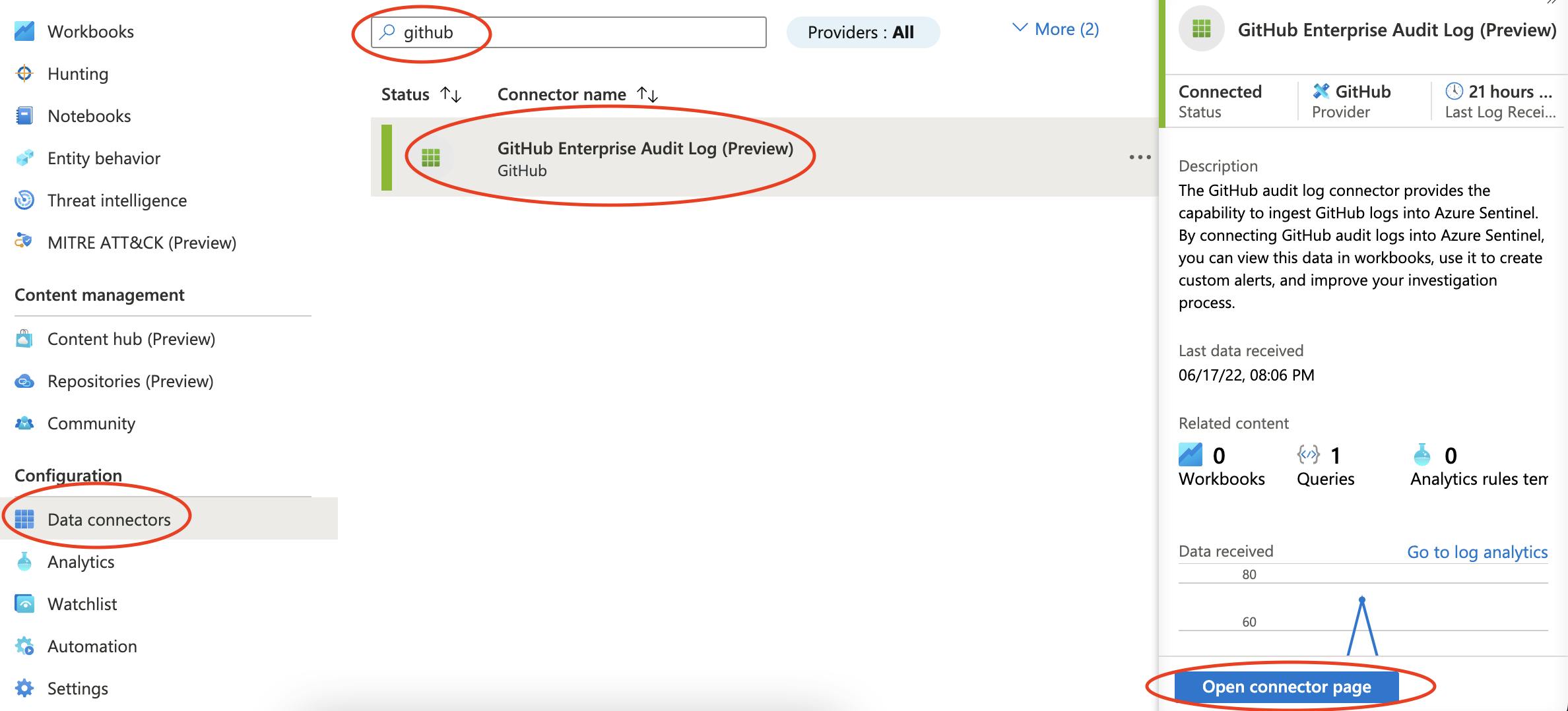
Now we are ready to connect Microsoft Sentinel to GitHub. You will need to load your Sentinel instance and go into the Data connectors blade by selecting the option in the side menu. Then you want to search GitHub and select the GitHub Enterprise Audit Log (Preview) option. On the right of the window, you will see a button with the name Open connector page; click it.
We need to populate the Organisation Name field with the GitHub organisation name and the API field with the PAT we generated. When ready, select Connect.
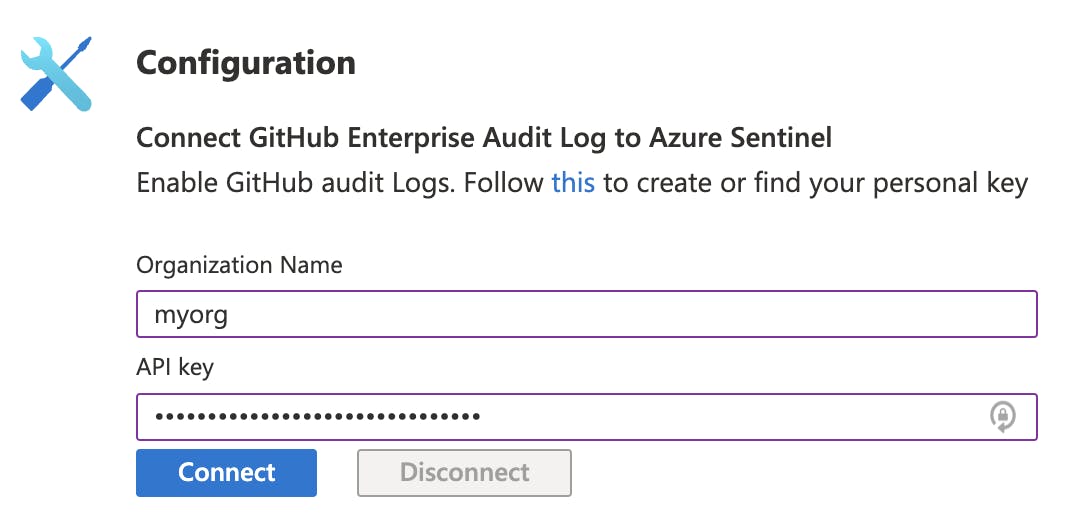
Once the action completes, Connected successfully message will display.
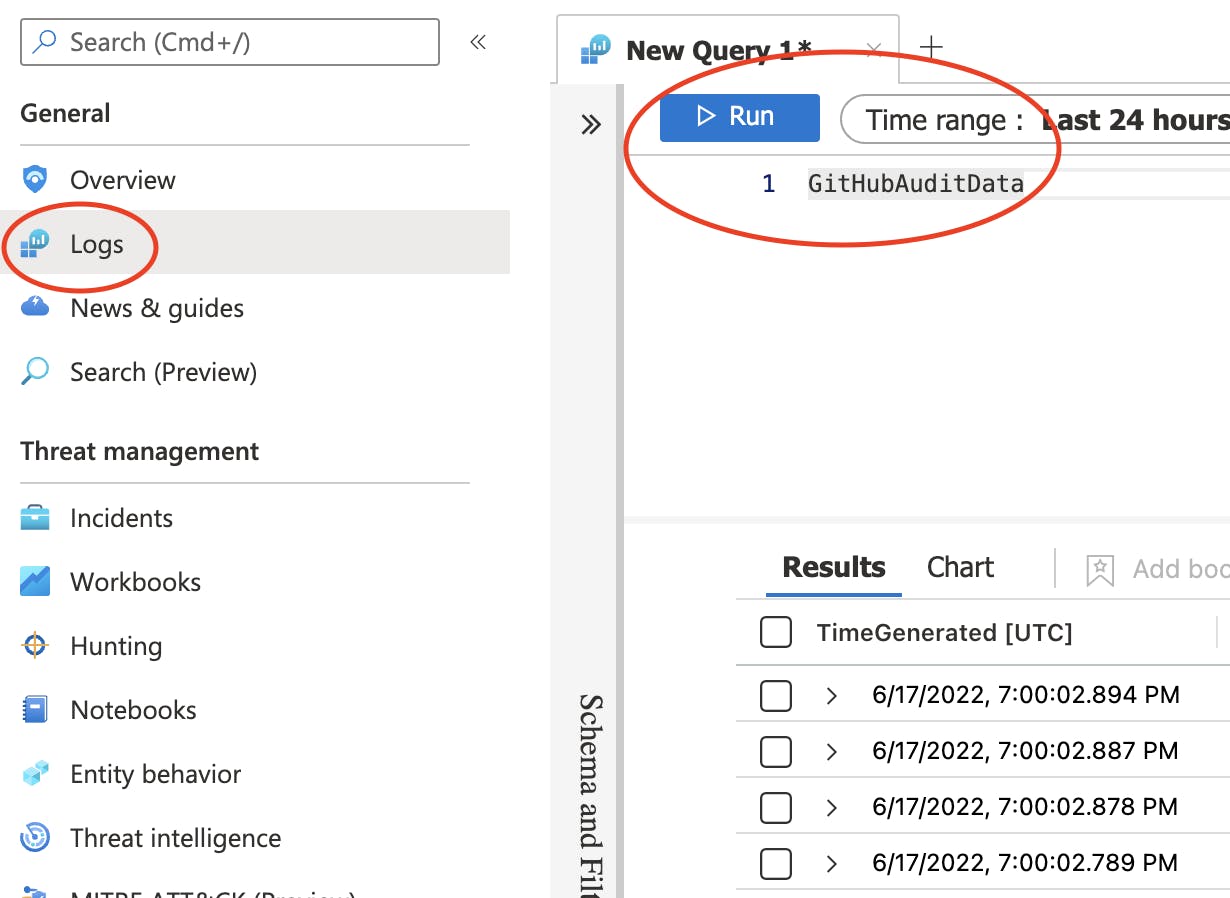
Check Logs
Allow some time (approx. 1 hour) and perform some admin action in the organisation to generate some audit logs. We will then use this to test if the connection is working.
Go into the Logs blade within Microsoft Sentinel and query GitHubAuditData. When executed, you will see some results, confirming the log data is collating as intended.