Did you know you can connect Azure DevOps audit logs to Microsoft Sentinel and create detection rules and automated responses? You might have heard me speak at the Microsoft Scottish Summit (2022) about this topic and wanted to read more about it or implement this in your organisation.
This blog post will walk you through how to connect Azure DevOps to Microsoft Sentinel. I will follow up with other blog posts that will cover how to create detection rules, automated responses and alerts. I will also cover GitHub, so make sure you subscribe to the blog or follow me on Twitter or LinkedIn.
Prerequisites
- Admin access to Azure DevOps
- Admin access to Microsoft Sentinel
- Azure Active Directory (Azure AD) must be connected to Azure DevOps to enable the Auditing feature. More information can be found here
Log Analytics
You will need the following information from your Log Analytics Workspace that's connected to Microsoft Sentinel:
- Workspace ID - you can find this from the Overview blade of the Log Analytics Workspace, under the Essentials section.

- Shared Key - this can be retrieved from the Agents Management blades within Log Analytics Workspace. You can choose the Primary Key or Secondary Key. Please remember that if you rotate a key that you are using, you will need to update Azure DevOps with the newly rotated key.

Enable Auditing
By default, Auditing is not enabled on Azure DevOps. To enable it, please ensure you have already connected Azure AD as mentioned in the prerequisites. Then you will need to select Organization settings from the dashboard of Azure DevOps.

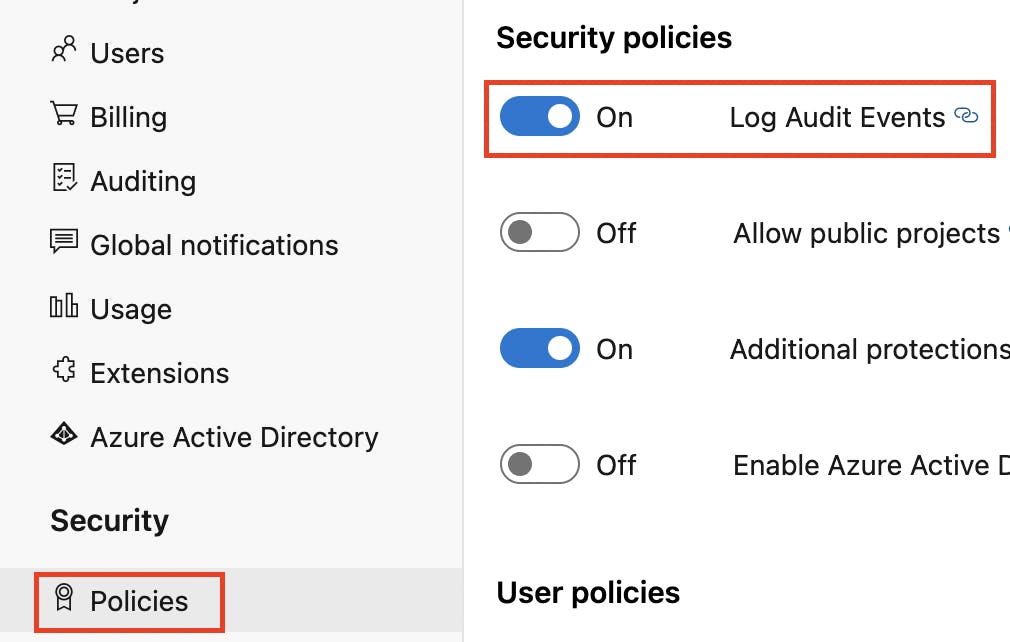
Then under the Security heading within the left side menu, select Policies. Toggle Log Audit Events to enable Auditing.
Link Audit Logs to Log Analytics
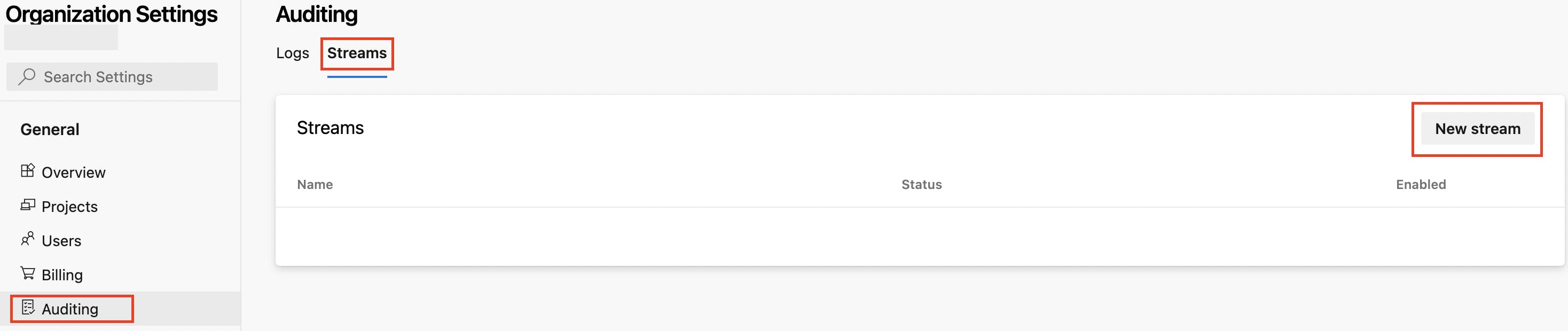
Now we have Log Audit Events toggled on; we should see a new option within the left side menu called Auditing. Select this and then the tab Streams. Here you can select New Stream
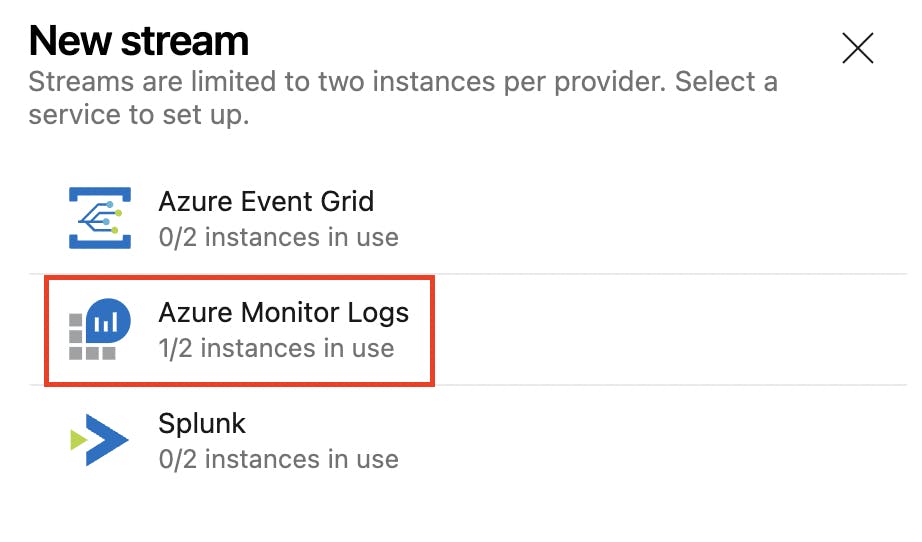
A new panel will appear with the options Azure Event Grid, Azure Monitor Logs, and Splunk. Select Azure Monitor Logs.
We now need to enter the Workspace ID we took from Log Analytics Workspace into the Azure Monitor Logs Workspace Id field and Shared Key into the Azure Monitor Logs Shared Key field.
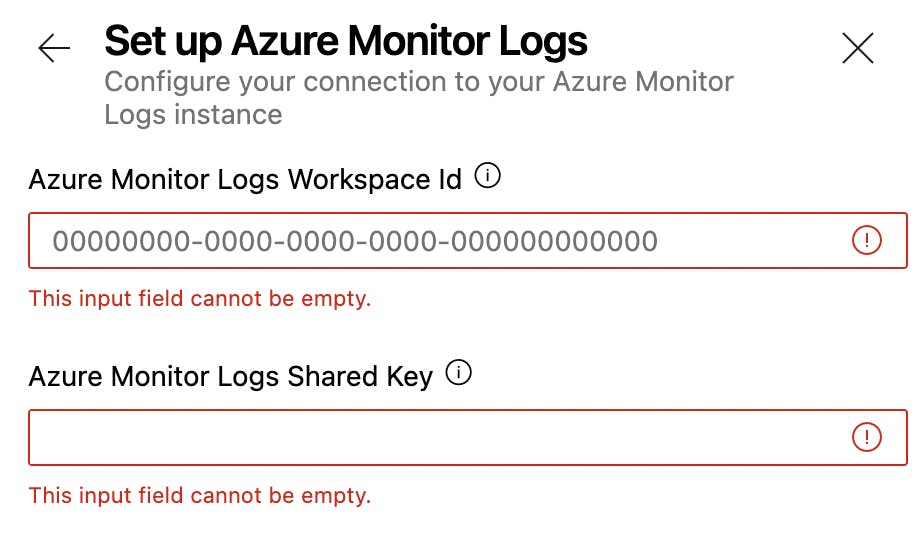
Once ready, select the Setup button at the bottom right of the window.
Checking Logs are being received
Now you connected Azure DevOps with Microsoft Sentinel. You need to check if the logs are being sent to the Log Analytics Workspace. To do this, allow a small amount of time to pass, and generate some logs by making minor amendments in the Organisation Settings, so they are recorded in Auditing.
Once you have done this, open your Log Analytics and go to the Logs blade
Type in the following query: AzureDevOpsAuditing
That's it, and select Run
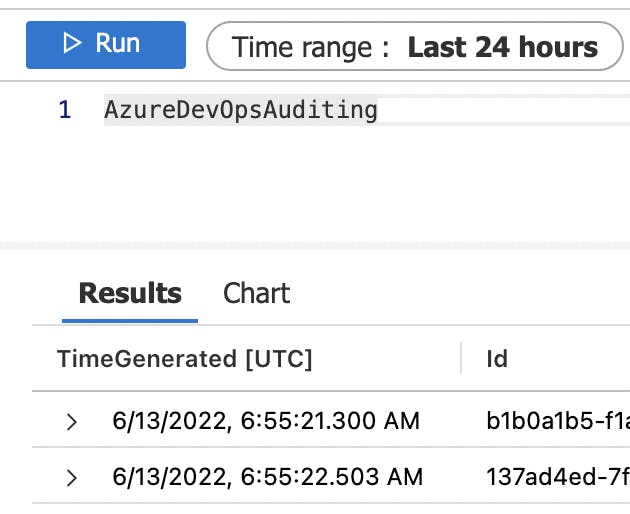
You should see some logs available. As long as the Log Analytics Workspace is linked to Microsoft Sentinel, you can use it for hunting and detecting.